How to deploy an image on K8SaaS with TrustNest IAM Service Account
If you are not familiar with Service Account you can read this documentation here
-
To start you will need to acquire a service account from TrustNest IAM
-
Then onboard your
service accountinto yourActive Directory Group.- If you are not familiar you with the process you can follow the documentation here
- In the past, you needed to extract the kubeconfig from the K8S internal Service account but this won't be necessary anymore.
Be sure to onboard your Service account with at least one of the 2 groups.
k8saas-<INSTANCE_NAME>-k8saas-developer-cluster-rolek8saas-<INSTANCE_NAME>-k8saas-devops-cluster-role
Otherwise you will not be able to deploy on your cluster.
-
Add these variable in your gitlab-ci.yml
- AKS_VERSION: <AKS_VERSION_OF_YOUR_CLUSTER> #e.g. 1.26.6
- INSTANCE_NAME: k8saas-<YOUR_CLUSTER_NAME> #e.g. k8saas-rbo-sandbox
- K8SAAS_DEPLOY_IMAGE: artifactory.thalesdigital.io/docker-public/k8saas/az-cli-helm
- SVC_ACCOUNT_SECRET_BASE64: "$SVC_ACCOUNT_SECRET_BASE64"tipThe AKS version of your cluster can be found on grafana, here's how you to access Grafana
-
Change
image: dtzar/helm-kubectl:$HELM_VERSIONtoimage: $K8SAAS_DEPLOY_IMAGE:$AKS_VERSION -
Then in the
before script:- Remove any reference to
KUBECONFIGas these will be deprecated.
...
- echo ${KUBE_CONFIG_K8SAAS} | base64 -d > ${KUBECONFIG}
- export KUBECONFIG=${KUBECONFIG}
...- Insert these line:
...
- export SVC_ACCOUNT_SECRET=$(echo "$SVC_ACCOUNT_SECRET_BASE64" | base64 -d)
- az login -u "$SVC_ACCOUNT" -p "$SVC_ACCOUNT_SECRET" --tenant "$TENANT"
- az aks get-credentials --name k8saas-"$INSTANCE_NAME" --resource-group k8saas-"$INSTANCE_NAME" && kubelogin convert-kubeconfig -l azurecli
... - Remove any reference to
This is an exemple to help you understand what to do:
image: nginx:latest
stages:
- build-docker
- deploy_aks
variables:
AKS_VERSION: "1.26.6"
INSTANCE_NAME: "rbo-sandbox"
K8SAAS_DEPLOY_IMAGE: artifactory.thalesdigital.io/docker-public/k8saas/az-cli-helm
SVC_ACCOUNT_SECRET_BASE64: "$SVC_ACCOUNT_SECRET_BASE64"
build-docker:
stage: build-docker
image:
name: gcr.io/kaniko-project/executor:debug
entrypoint: [""]
script:
- mkdir -p /kaniko/.docker
- echo "$CI_COMMIT_TAG"
- echo "{\"auths\":{\"$ARTIFACTORY_URL\":{\"username\":\"$ARTIFACTORY_USER\",\"password\":\"$ARTIFACTORY_PASSWORD\"}}}" > /kaniko/.docker/config.json
- /kaniko/executor --context $CI_PROJECT_DIR --dockerfile $CI_PROJECT_DIR/Dockerfile --destination K8SAAS_DEPLOY_IMAGE:$CI_COMMIT_SHA
deploy_aks:
stage: deploy_aks
image: $K8SAAS_DEPLOY_IMAGE:$AKS_VERSION
before_script:
- export SVC_ACCOUNT_SECRET=$(echo "$SVC_ACCOUNT_SECRET_BASE64" | base64 -d)
- az login -u "$SVC_ACCOUNT" -p "$SVC_ACCOUNT_SECRET" --tenant "$TENANT"
- az aks get-credentials --name k8saas-"$INSTANCE_NAME" --resource-group k8saas-"$INSTANCE_NAME" && kubelogin convert-kubeconfig -l azurecli
- cd helloworld
script:
- echo Starting
- echo " >>>>>>>>>> Deploy in progress for $CI_PROJECT_NAME <<<<<<<<<< "
- >
helm install helloworld
--namespace customer-namespaces
--timeout 2m
--wait .
- Add these variable in your project CICD variables
-
SVC_ACCOUNT
- This will be the name of your service account you requested to Trustnest IAM
-
SVC_ACCOUNT_SECRET_BASE64
- The secret that was shared with the service account. Be sure to tick the masked variable.
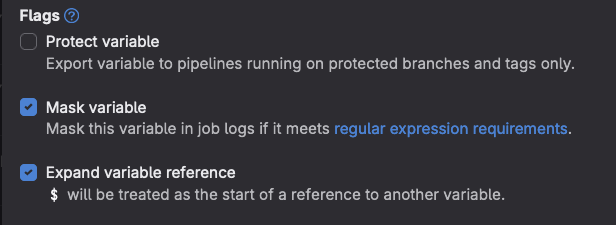
-
TENANT
- Thalesdigital.io tenant -
737c6905-f186-4bcf-afb3-43e349ee23a3
- Thalesdigital.io tenant -
-
- Launch your pipeline and look at the log, you should have something similar to this confirming it's now using your
Trustnest IAM Service Account:
Executing "step_script" stage of the job script
$ export SVC_ACCOUNT_SECRET=$(echo "$SVC_ACCOUNT_SECRET_BASE64" | base64 -d)
$ az login -u "$SVC_ACCOUNT" -p $SVC_ACCOUNT_SECRET --tenant "$TENANT"
[
{
"cloudName": "AzureCloud",
"homeTenantId": "737c6905-f186-4bcf-afb3-43e349ee23a3",
"id": "2927a8a3-7ed8-4c24-a9a4-d7b4c65600e2",
"isDefault": true,
"managedByTenants": [],
"name": "MVP-TDF-K8SAAS-TEST",
"state": "Enabled",
"tenantId": "737c6905-f186-4bcf-afb3-43e349ee23a3",
"user": {
"name": "MCS-MANAGED-SERVICES-rbo-mcs@svc.thalesdigital.io",
"type": "user"
}
},
{
"cloudName": "AzureCloud",
"homeTenantId": "737c6905-f186-4bcf-afb3-43e349ee23a3",
"id": "61ed80ee-27d4-4f1f-adf0-7a6c5a83f9bc",
"isDefault": false,
"managedByTenants": [],
"name": "COS-IT-SRE-PRD-Services",
"state": "Enabled",
"tenantId": "737c6905-f186-4bcf-afb3-43e349ee23a3",
"user": {
"name": "MCS-MANAGED-SERVICES-rbo-mcs@svc.thalesdigital.io",
"type": "user"
}
}
]
$ az aks get-credentials --name k8saas-"$INSTANCE_NAME" --resource-group k8saas-"$INSTANCE_NAME" && kubelogin convert-kubeconfig -l azurecli
WARNING: Merged "k8saas-rbo-diag2-sandbox" as current context in /root/.kube/config
Don't forget to update $SVC_ACCOUNT_SECRET, whenever you are asked to renew the account credential.