Private application exposition with Nginx
Context
When a team is beginning a development, the component may not be secured enough. Exposing this application on internet during the development phase is not a good practice.
K8Saas provides a private ingress that allow you to expose your application internally. It means that your containers will be exposed using an ingress, but the IP will be private (meaning, the IP will be part of the AKS vnet).
To access to your internal containers, you should:
- use a VPN (such as Zscaler provided by trustnest platform)
- use a peered Vnet to AKS
Use case
- PoC with a low security level
- Hybrid architecture (on-prem & cloud)
- MFA not supported by a containerized application
Archicture
Kubernetes Landing Zone offers several ways to expose an application:
- a default nginx ingress controller (in orange)
- an internal nginx ingress controller (in light green)
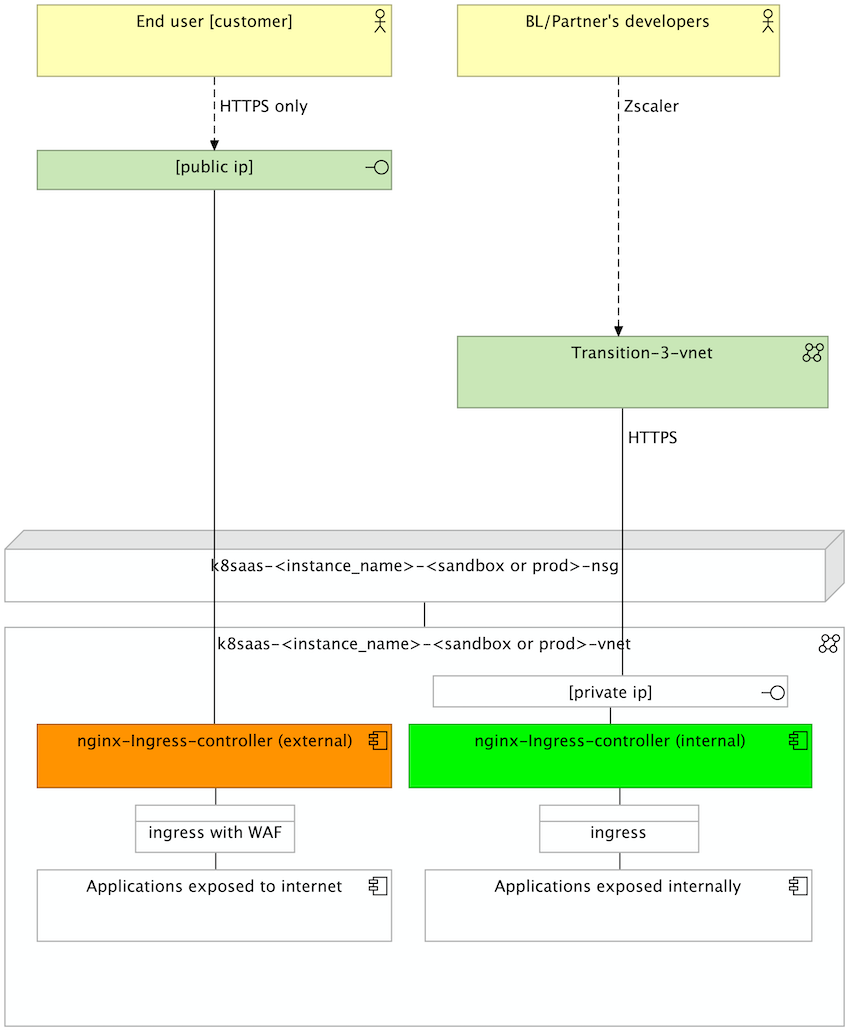
The default nginx ingress controller uses an azure load balancer to expose your application to internet. Here the network flow of an enduser who access to the application.
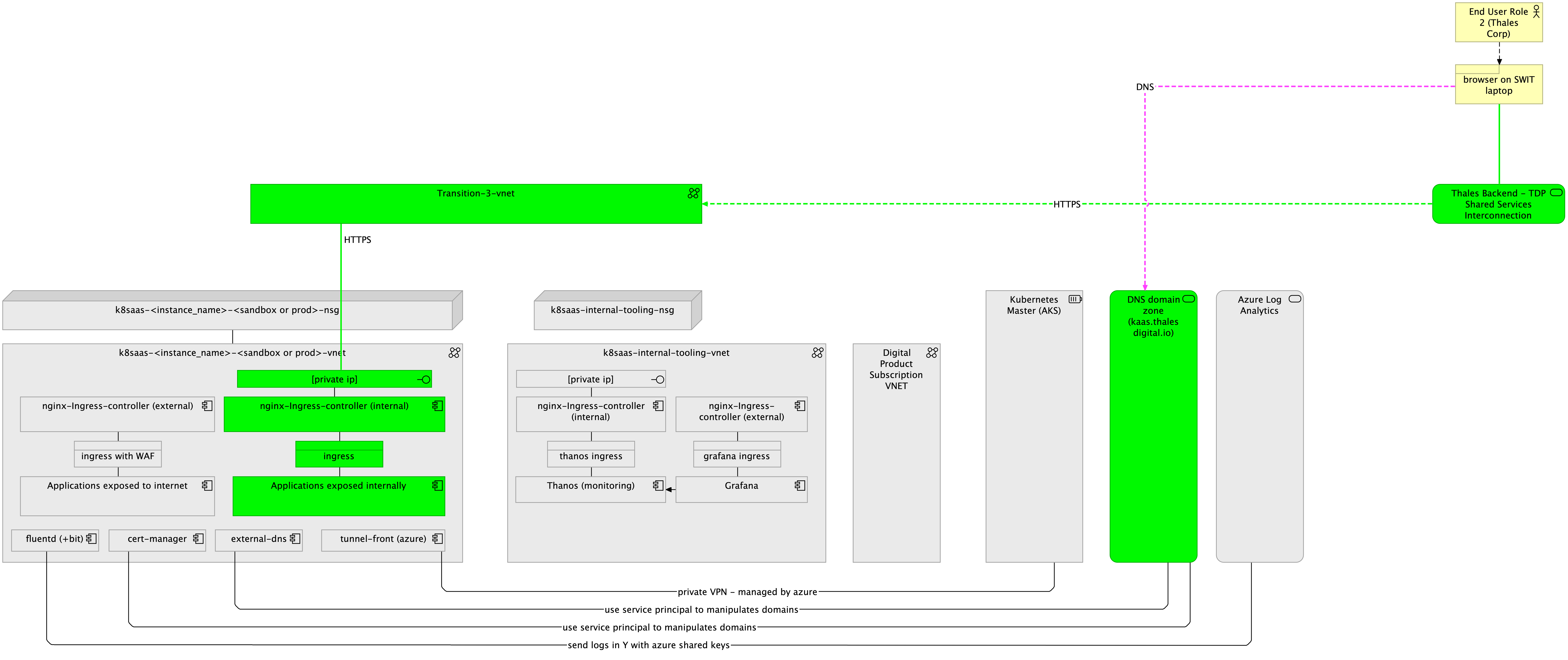
During the development, It may happen to have unsecured applications (default password, testing mode etc...). In this case, it is recommended to exposed your application internally. With this configuration you must have a correct VPN setup to access to the shared services.
If you're part of the Thales Digital Factory:
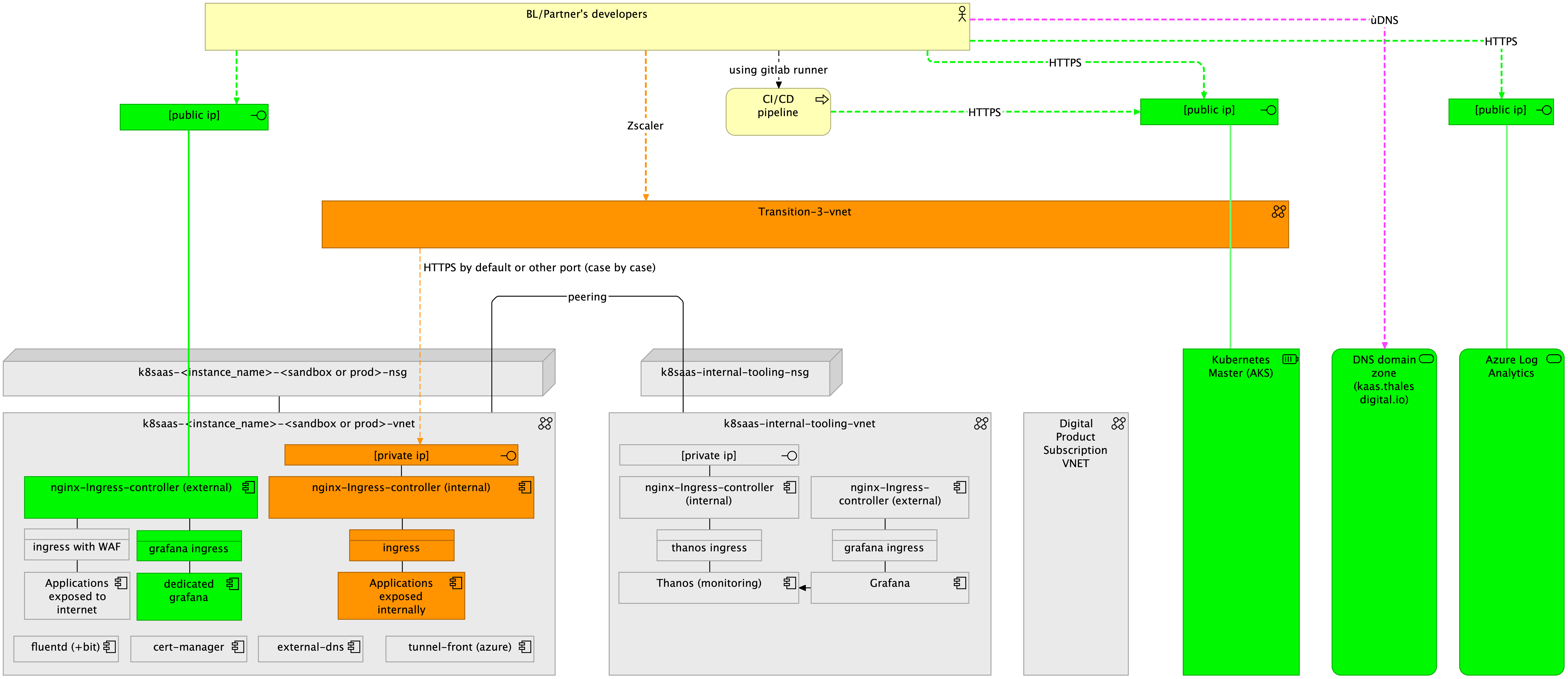
Or part of the Thales Corporate network:
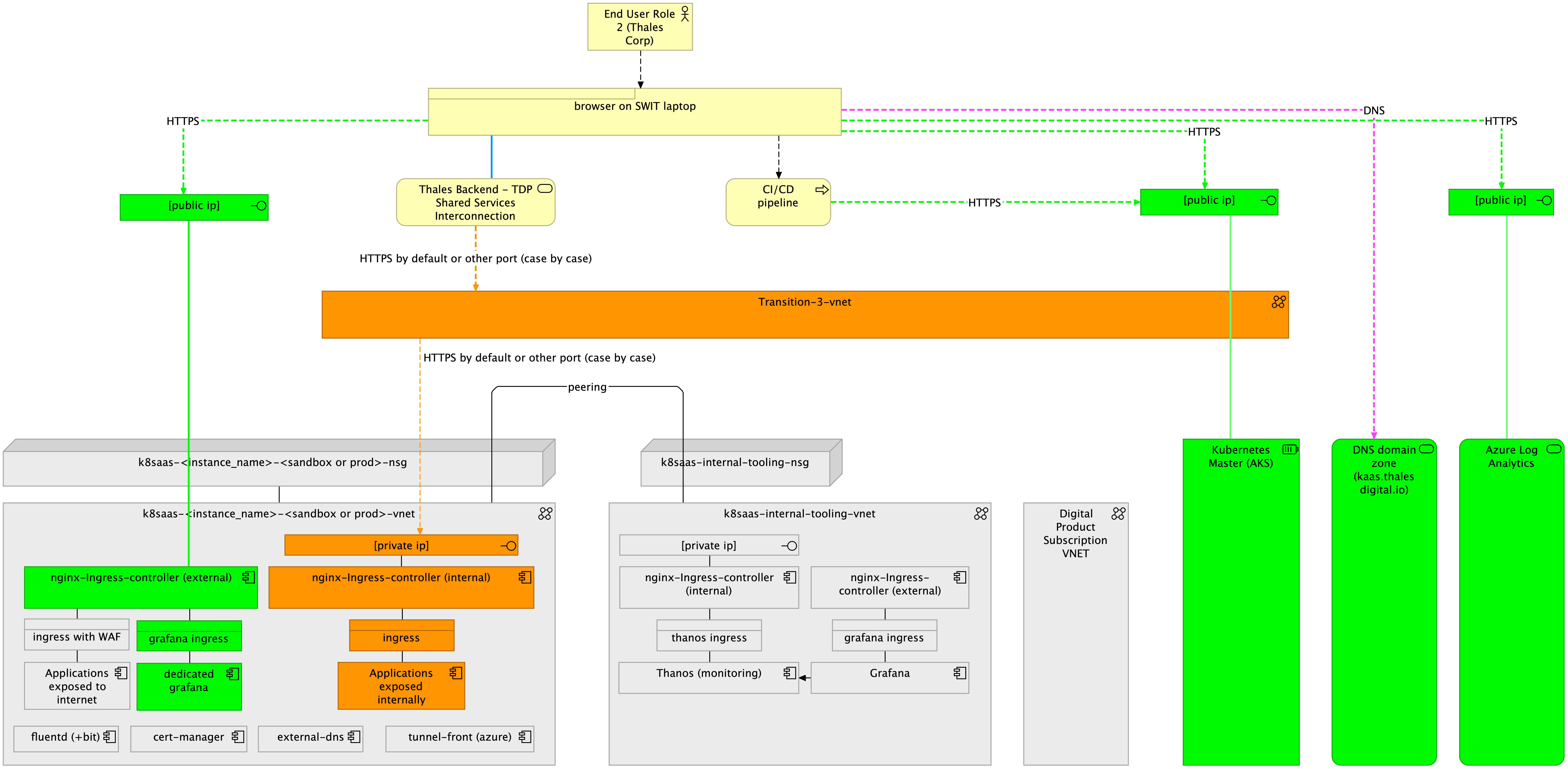
HOWTO
Configure your application to use the right nginx ingress controller ?
The 2 controllers are deployed with a specific class:
- nginx for the default controller
- nginx-internal for the internal controller
Let's take an example: https://gitlab.thalesdigital.io/platform-team-canada/k8saas-innersource/hello-world-k8saas/-/blob/master/Basic-helloworld/hello-world-ingress.yaml
The ingress of the hello world uses the default class:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: hello-world-ingress
annotations:
cert-manager.io/cluster-issuer: letsencrypt-prod
spec:
ingressClassName: nginx
tls:
- hosts:
- hello-world-ingress.demo.kaas.thalesdigital.io
secretName: tls-hellow-world
to use the internal ingress, you just have to update the ingressClassName (and redeploy your ingress), like:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: hello-world-ingress
annotations:
cert-manager.io/cluster-issuer: letsencrypt-prod
spec:
ingressClassName: nginx-internal
tls:
- hosts:
- hello-world-ingress.demo.kaas.thalesdigital.io
secretName: tls-internal-hello-world